If you have logged in recently with your Apple ID and requested an SMS-based second-factor verification code instead of using the trusted device method, you might have noticed Apple made a change to the text you receive.
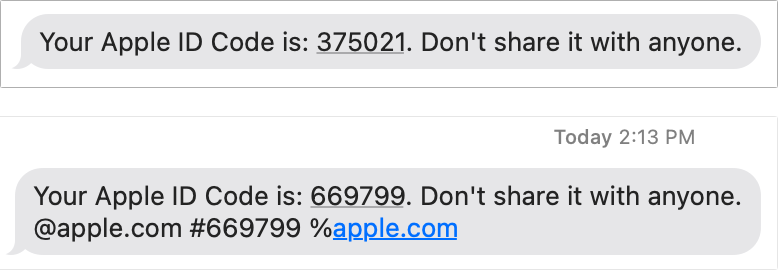
Previously, Apple sent a message like this:
Your Apple ID Code is 123456. Don’t share it with anyone.
Starting around November 2021, the codes appear in this format:
Your Apple ID Code is: 123456. Don’t share it with anyone. @apple.com #123456 %apple.com
Why the change? Apple proposed in August 2020 that it would support “domain-bound codes” for logins. This kind of code requires sites make a slight addition to the text messages used for verification codes. The incoming message has to provide a destination domain and some other data. Apple said that this change would improve the integrity of its operating systems offering to autofill the code via a suggestion in the QuickType bar in iOS and iPadOS and a drop-down value in macOS Safari and other macOS apps that take advantage of this feature.
Apple proposed this change as a way to deter phishing that tries to intercept and redirect verification codes. In most phishing attacks, the victim gets directed to a fake site that asks them to enter their credentials. The site takes those credentials and silently relays them to login at the legitimate site.
But some attackers are wise to two-factor authentication. If the site sends a code via SMS as the default method, the user being phished receives a text message with the code. The phisher then prompts for that code.
iOS, iPadOS, and macOS offer to fill in the code most recently arrived via SMS to the Messages app in any properly formatted field—including a phishing site’s verification-code field. That makes it too easy on the scammers.
However, if the text message is scoped as Apple suggested, operating systems starting with iOS 15, iPadOS 15, and macOS 11 Big Sur will only offer to autofill on sites that match the domain name. The security isn’t perfect, but it’s a simple update to beef up defensive actions.
The format generally looks like this:
- A standard human-readable message, including the code, followed by a new line.
- The scoped domain as
@domain.tld. - The code repeated again as
#123456. - If the site uses an embedded HTML element, called an iframe, the source of the iframe is listed after %, such as
%ecommerce.example. (The original spec specifies @; Apple appears to be using % for its texts.)
As a user, there’s nothing you need to do. The SMS codes continue to autofill as expected for valid sites.
However, you can exercise increased vigilance: when you receive a code in this format as a text message and your app or browser doesn’t offer to autofill it, you could be subject to a phishing trap. Investigate the domain or app carefully before proceeding.
This Mac 911 article is in response to a question submitted by Macworld reader Kevin.
Ask Mac 911
We’ve compiled a list of the questions we get asked most frequently, along with answers and links to columns: read our super FAQ to see if your question is covered. If not, we’re always looking for new problems to solve! Email yours to mac911@macworld.com, including screen captures as appropriate and whether you want your full name used. Not every question will be answered, we don’t reply to email, and we cannot provide direct troubleshooting advice.
from Macworld.com https://ift.tt/mj7lVS5C8
via IFTTT